Keywords
|
| Internet banking; Technology acceptance; Technology interface; Structural Equation Modeling; research study; India |
INTRODUCTION
|
| Information technology has been pervasive in our day to day life. Whether it is in the form of a computer, hand held devices or online services, information technology affects our day to day routines right from home to workplace and to other places for various purposes. According to Meuter et al.(2000) , there is a significant growth in the number of customers interacting with the technology interfaces provided by the firms and hence the technology interfaces have become the key criterion for business success. |
| However not all technology interfaces are accepted or used by the users. There are various beliefs/reasons why users use a particular technology interface (Information technology and technology may be taken synonyms). Customers seem to assess the different features/characteristics of technological interface and also look for the quality of information provided by the technological interface. This assessment seems to be more critical when a financial transaction has to be carried out through the interface. For instance, customers seem to be apprehensive while sharing sensitive information such as credit card or debit card numbers over the Internet. Unless they are convinced that the information they reveal is protected and not misused, they will not try to carry out any financial transaction. |
| Other than security issues, there could be various other reasons behind the usage of technological interfaces such as user friendliness of the interface in terms of information organization, smooth navigation and information retrieval according to the needs of the customers. Creators and investors of technology need information about the consumers’ assessment of their technology based on the features and various quality dimensions to make strategic decisions in bringing out technological interfaces and compete on various quality dimensions. For instance, banks in India such as ICICI Bank, HDFC Bank have implemented https (hypertext transfer protocol security) in their Internet banking interface, to make transactions more secure in their interface and build confidence among their customers. Recently, ICICI Bank has introduced a new feature i-safe in their Internet banking interface , which is an enhanced security system that protects customer’s account whenever a change in the Internet banking login and transaction patterns are observed. There are also instances of providing interactive support through Interactive voice responses in self-servicing technologies which addresses certain needs of the customer and at the same time relieves the pressure on the human employees in an organization and also reduces the transaction cost of the organization. |
| From past literature it can be inferred that in case of technology interfaces through the Internet, web site features and information integrity are the two important aspects to be considered. Some of the website features like organization of information, customization, support, trust are discussed in the literature of website usability and website quality evaluation. Security, privacy, risk and trust were identified as the concerns in adopting transactional websites like Internet banking in other studies. In this study, a model is developed relating the end user beliefs about the technological dimensions of the IT interface through the Internet, and their beliefs about the utility about the IT interface and the usage of the interface. The moderating effect of the user demographics and situational factors on the relationship between the beliefs about the technological dimensions and then utility is also considered in the study. |
LITERATURE REVIEW
|
| A review of research studies related to acceptance of technology is presented in this section. This review helped in building a generic framework, which was subsequently taken up for study. The research studies are broadly discussed under two groups. These groups are Technology Acceptance Model and Extensions to Technology Acceptance Model. |
Technology Acceptance Model (TAM)
|
| Davis (1989) adapted Theory of Reasoned Action to develop a model for acceptance or usage of technology. Davis developed and validated measures for two beliefs viz. Perceived Usefulness and Perceived Ease of Use of the technology which predicted the usage of technology. According to Davis, Perceived Usefulness was defined as the “degree to which a person believes that using a particular system would enhance his or her job performance”; Perceived Ease of Use was defined as “the degree to which a person believes that using a particular system would be free of effort. |
Extensions to TAM
|
| TAM was considered inadequate by Moore and Benbasat(1991) to explain the adoption of IT innovations as there were some more characteristics of IT innovation to be considered other than Perceived Usefulness and Ease of Use .The authors carried out a study to develop and validate measures for characteristics of IT innovation which will discriminate adopters and non-adopters of IT innovation. A study was carried out by Davis (1993) to examine the effect of system design features on end user acceptance of a system. Agarwal and Prasad (1999) considered individual user differences as external variables to the TAM, in their study. They suggested that Ease of Use and Usefulness beliefs of an individual fully mediate the influence of selected individual difference variables on attitude and usage intentions. Venkatesh(2000) carried out three longitudinal field studies to test the model of determinants of Perceived Ease of Use. The antecedents included the anchors and the adjustments. Anchors determined the early perceptions of ease of use. Adjustments resulted from user-system interaction and could shape Perceived Ease of Use over time. Computer self-efficacy, perceptions of external control, computer anxiety, computer playfulness which were considered as anchors; and Perceived enjoyment, objective usability were treated as adjustments. On similar lines, Venkatesh and Davis (2000) proposed Subjective norms, Image, Job Relevance, Output Quality and Result Demonstrability as determinants of Perceived Usefulness. Venkatesh(2000) discussed the determinants of perceived ease of use. Venkatesh and Davis (2000) discussed the determinants of perceived usefulness which is also described as TAM2. Both the models were integrated and developed by Venkatesh and Bala(2008). The integrated model was called by the authors as TAM3. TAM and its extensions were not only restricted to acceptance of technology in organization settings. There are numerous studies using TAM and extending TAM to technologies used in non-organization settings. |
Literature gap
|
| TAM captures the user motivations behind the use of technology. These user motivations are Perceived Ease of Use and Perceived Usefulness. However the information regarding these motives does not give specific feedback to the designers of the technology based on which they can work further towards improvement of the technology. Usage and user motivations can be influenced through the design of technology itself. This view is consistent with the views of Venkatesh and Bala (2008), Wixom and Todd (2005), Orlikowski and Iacono (2001). Also Davis et al. (1989) suggested that external stimuli such as environment policies, system characteristics are important and its effect on the perceptions which in turn affects behavioral response are to be considered. From the review of the literature, it can be seen that TAM incorporates external stimuli like individual differences, situational factors and system characteristics. There is a need to identify specific dimensions of technology characteristics and study the influence of user perceptions of these dimensions on the user motivations. Moreover there is a need to examine the interaction between perceptions of specific dimensions of technology with perceptions about situational factors. |
| The interaction between perceptions of specific dimensions of technology with individual user differences. |
| This will give insights to the managers on designing appropriate interventions based on significant interactions. This will give insights to managers on the technology characteristics which need improvement. |
RESEARCH OBJECTIVES
|
| The objectives of the proposed research based on research gaps identified are as follows |
| • To identify the dimensions of the technology interface characteristics |
| • To study the relationship between technology interface characteristics, technology utility and usage |
| • To study the influence of user demographics and technology comfort on the relationships stated in the second objective |
CONCEPTUAL FRAMEWORK
|
| To achieve these objectives, a research model was developed based on the conceptual framework. Fishbein and Ajzen (1975) developed a theory on the relationships between different types of beliefs. According to them there are different types of beliefs namely descriptive and inferential The conceptual framework related the descriptive, inferential beliefs and informational beliefs about the technology. The descriptive beliefs were the end-user’s perception of technology interface characteristics. The inferential beliefs were the end-user’s perception of the utility of technology interface. Beliefs other than descriptive beliefs which influence inferential beliefs are called as informational beliefs. The relationship between the descriptive beliefs and the inferential beliefs can be treated as function of the informational belief. |
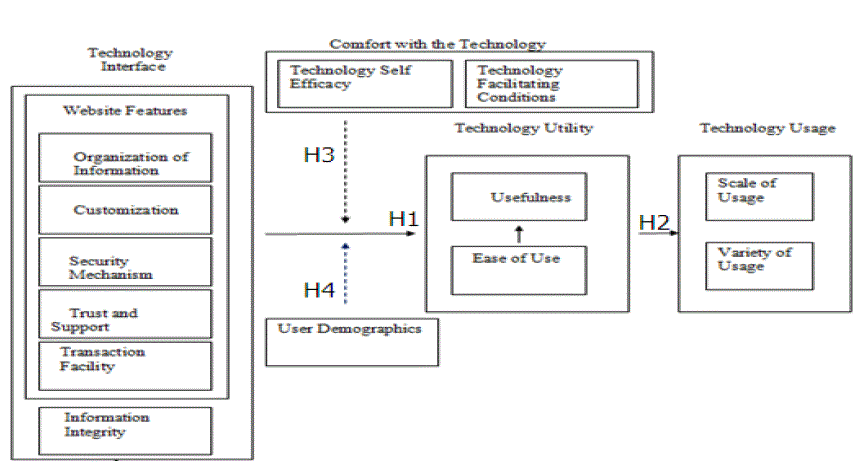
| Based on the framework, the research model is developed which relates user perceptions of technology interface characteristics, user perception of technology comfort, user perception of technology utility and technology usage as shown in Figure 1. |
RESEARCH HYPOTHESES
|
| The dimensions of Technology Interface Characteristics, Technology Utility and Technology Usage had to be identified and confirmed, prior to testing of the hypotheses discussed in this section. |
| According to Ratneshwar et al. (1999) when a person uses a technology, the user mentally translates the characteristics of the technology to the benefits and effort required by the user as to carry out the tasks The usage will depend on the benefits gained and effort the user has to put in using the technology. This forms the basis for formulating the following hypotheses |
| H1: The dimensions of Technology interface characteristics positively influence the dimensions of Technology Utility. |
| H2: The dimensions of Technology Utility positively influence the dimensions of Technology Usage. |
| When a person uses a technology whose characteristics are not highly rated by the person, but still the person may perceive higher utility out of the technology, if the person believes that the person can extract most out of the technology. The same holds good for the low rated technology where the facilitating conditions are good enough to extract utility. Similarly even if the technology is highly rated, the person may not perceive any utility because of lack of confidence in person’s ability to use them or the person has not got enough support to bring down person’s apprehension. This forms the basis for formulating the following hypothesis |
| H3: The dimensions of Comfort with the Technology moderate the influence of Technology interface dimensions on the dimensions of Technology Utility |
| User demographics refer to age, gender, education level, experience in using technology, and access to the technology. Individuals will rate the characteristics of the technology differently based on their exposure to the technology, the environment in which they experience the technology. So they tend to perceive different levels of utility from the technology. This forms the basis for formulating the following hypothesis. |
| H4: User Demographics moderate the influence of Technology interface dimensions on the dimensions of Technology Utility. |
DATA COLLECTION AND METHODOLOGY
|
| The study was conducted in the context of Internet Banking. Internet Banking could be considered as one of the rising information intensive technologies that use Internet as a remote delivery channel for banking services for seeking information and conducting transactions. To understand end-users’ perceptions, knowledge, beliefs and preference about the Internet Banking Interface, the survey research approach was undertaken. The retail Internet banking users constituted the sampling unit for the survey. |
| A structured questionnaire was designed for the purpose of collecting information and was administered online. Most of the items of the questionnaire were adapted from past literature. . The items were adapted from literature on Website Design ((Palmer, 2002), (Loiacano et al., 2007)), Security and Trust (Tsiakis and Sthephanides, 2005). Items regarding Customization, Security, Trust and Support, Transaction Facility were developed in the context of Internet banking and pooled to the existing list of items after discussion with Internet banking users of different banks. The items for Information Integrity were suitably adapted from Information Quality scale given in Lee et al. (2002).The items for the constructs in the Technology Utility were adapted from Davis (1989). The items of the Technology Usage were adapted from Igbaria et al. (1995). The items for the constructs in the Comfort with the Technology were adapted from Venkatesh (2000). User Demographic variables, namely, age, gender, profession were captured through a nominal scale whereas monthly household income, educational level, Internet banking experience was captured through ordinal scale. The User Demographic variables were used in profiling and multi-group analysis. |
| Initially, the link to the questionnaire was e-mailed to a mailing list of known people. They were also requested to forward the mail to the people whom they know who are using Internet banking. Besides sending e-mails, the link of the questionnaire was also placed in various social networking sites like Facebook and Orkut and personal website of the researcher. Responses were also obtained offline on the paper-based questionnaire from a sample of Internet users. |
Information was obtained from 265 respondents over a period of four months. Respondents were subsequently filtered to 250 in the data cleaning process.
Exploratory Factor Analysis (EFA) was used in this research study to identify the various dimensions of Technology Interface Characteristics. Confirmatory Factor Analysis (CFA) was used to validate the measured model. The Hypotheses H1 and H2 indicated earlier were tested using path coefficients obtained from Path Analysis (PA). |
| The Hypotheses involving the moderating or interaction effect of the constructs (H3) and the Hypotheses involving the User demographics as moderators (H4) were tested using multi-group analysis. |
DATA ANALYSIS AND INTERPRETATION
|
| The first objective of this research study is to identify the dimensions of Technology Interface Characteristics (TIC).To meet this objective, exploratory factor analysis (EFA) was carried out with the responses to the questionnaire items. Principal Component Analysis with Oblimin rotation method was used in obtaining factors. |
| This process was carried out iteratively until the factors obtained could be interpreted meaningfully. As a result, 9 factors were extracted from 25 questionnaire items which explained 78.04% of total variance. 9 items were removed from the initial pool of 34 questionnaire items on account of either cross loading or very insignificant loading. The measure of internal consistency, coefficient alpha, was also computed for the items with the given factor. Coefficient alpha for each of the factors was closer to 0.7 or greater which is acceptable according to the recommendation from Nunnally (1978). According to the results, the dimensions of TIC are Organization of Information (Orgf), Customization (Cust), Security (Sec), Transaction Facility (TF) and Information Integrity (InfI). Usefulness (USEF) constitutes the sole dimension of Technology Utility (TUt). Self Efficacy (SE) and Facilitating Conditions (FC) constitute the dimensions of Comfort with the Technology (CT). Usage (Usage) constitutes the sole dimension of Technology Usage (TU). |
| The factors obtained and the internal consistency of the items within a factor is shown in Table I. |
Since the factors obtained represented the constructs in the research model, Confirmatory Factor Analysis (CFA) was carried out to confirm that the items logically and systematically represented the constructs in the research model. AMOS 16.0 Software was used to carry out the CFA. To assess the convergent and discriminant validity of the constructs, the average variance extracted (AVE) by the items within the construct and shown in Table II. According to Hair et al. (2006)AVE estimates should be 0.5 or greater to suggest adequate convergent validity
AVE estimates for two factors should be greater than the square of the correlation between the two factors to indicate discriminant validity., |
| The values given in Table II are acceptable according to the above recommendations. |
| The model fit was also evaluated on the basis of multiple indices as given in Table III. The Table also gives the recommended values for the indices as suggested by Hair et al. (2006). The values of the indices for the measurement model is in compliance with the recommended values which indicates a good fit. |
| To test the hypotheses, a structural model was constructed. In this model, the dimensions of Technology Interface Characteristics were considered as predictors of Usefulness which was a dimension of Technology Utility. Usefulness was considered as a predictor of Technology Usage. |
| The Model fit indices for the structural model fit are given in Table IV. |
| Comparing the values of the indices with the recommended values indicates that the structural model has a good fit.By examining the p-values given in Table V and the sign of the estimates, it can be inferred that there are significant positive relationship between |
| • Usefulness and Organization of Information at 1% significance level |
| • Usefulness and Information Integrity at 1% significance level |
| • Usefulness and Transaction Facility at 5% significance level |
| • Usage and Usefulness at 1% significance level |
| Self-Efficacy and Facilitating Conditions were considered as dimensions of Comfort with the Technology The mean scores of Self Efficacy and Facilitating Conditions for each respondent were calculated. High and low groups were formed based on proportion of the mean scores for Self Efficacy and Facilitating Conditions separately. Self-Efficacy and Facilitating Conditions were examined for the moderating effect separately. Hence multi-group analysis was carried out separately for each of the moderating variables. The procedure for carrying out Multi-group analysis was adapted from Dabholkar and Bagozzi(2002). |
| The values of Coefficient alpha for the constructs as indicated earlier showed satisfactory internal consistency. The mean of the respondent scores for the items in the construct could very well represent the construct score for each respondent and were used the regression model relating the dimensions of Technology Interface Characteristics and dimensions of Technology Utility |
| In case of both Self Efficacy and Facilitating Conditions, the regression estimates of the path between Security and Usefulness; and path between Customization and Usefulness were found to be insignificant for both high and low groups at 1% significance level. The comparison of constrained and unconstrained models as shown in Table VI indicated that Facilitating Conditions didn’t moderate the relationship whereas Self Efficacy moderated the relationship. |
| Since the p-value given in the table corresponding to Self Efficacy was significant at 5% significance level, individual paths were examined. The results of the individual path assessment for Self Efficacy as the moderator are given in Table VII |
| Since the p-value given in Table VII corresponding to path MeanInfIïÃÆàMeanUSEF was significant at 1% significance level, it could be inferred that Self Efficacy moderated the relationship between Information Integrity and Usefulness. To observe the direction of the moderation, the regression estimates of the unconstrained model for both the high and low groups were examined for the path. The regression estimates of the path for both the groups are given in Table VIII. |
| The regression estimate of the path between Information Integrity and Usefulness is higher for the end-users belonging to Low Self Efficacy group than for those belonging to High Self Efficacy group. |
| This suggests that Information Integrity should be more effectively maintained in the interface if the end users with less self-efficacy have to derive utility from the Internet banking interface. This helps in building confidence in those end users who are not confident to use the Internet banking interface on their own. |
In case of all demographic variables, the regression estimates of the path between Security and Usefulness; and path between Customization and Usefulness were found to be insignificant for both the groups at 1% significance level.
The results of the comparison of unconstrained and constrained models are given in Table IX. |
| Since the p-value given in Table IX corresponding to Gender was significant at 5% significance level and that of Age was significant at 10% significance level, individual paths were examined |
| In case of Gender, since the p-value given in Table X corresponding to path MeanOrgïÃÆàMeanUSEF was significant at 1% significance level, it could be inferred that Gender moderated the relationship between Organization of Information and Usefulness. |
| To observe the direction of the moderation in case of gender, the regression estimates of the unconstrained model for both male and female groups were examined for the path. The regression estimates of the path for both the groups are given in Table XI. |
| The regression estimate of the path between Organization of Information and Usefulness is higher for female end-users than for male end-users. This suggests that female end-users prefer to have organized information in the Internet banking interface than male end-users to derive more utility from the interface. |
| In case of Age, since the p-value given in Table XII corresponding to path MeanTFïÃÆàMeanUSEF was significant at 10% significance level, it could be inferred that Age moderated the relationship between Organization of Information and Usefulness. |
| To observe the direction of the moderation in case of age, the regression estimates of the unconstrained model for both the groups were examined for the path. The regression estimates of the path for both the groups are given in Table XIII. |
| The regression estimate of the path between Transaction Facility and Usefulness is higher for end-users whose age is less than or equal to 30 years than end-users whose age is greater than 30. This suggests that younger end-users prefer to have Transaction Facility in the Internet banking interface than end-users of older age group to derive more utility from the interface. |
CONCLUSIONS AND RECOMMENDATIONS
|
| The results of the exploratory factor analysis show that there are five dimensions of Technology interface characteristics as perceived by the end-users namely, Organization of Information, Customization, Security, Transaction Facility and Information Integrity. The result of the path analysis show that the user perception about Organization of Information, Transaction Facility and Information Integrity positively influence the user’s perception of Technology Utility. Technology Utility in turn positively influences Technology Usage. The interpretations of the results are given below. |
Relationship between Organization of Information and Technology Utility
|
| When the end-users find the interface easy to navigate, they may experience less mental effort to use the interface, which in turn may imply less cost. Utility is considered as the ratio of benefits to the cost. Since the cost of using the interface seems to be less in terms of mental effort, the utility of the interface may enhance. |
Relationship between Transaction Facility and Technology Utility
|
| The end-users tend to consider the Internet banking interface more useful when various transaction options are provided to them which they can carry out easily. The transaction options seem to be directly proportional to the benefits provided by the interface which may increase the Technology Utility. |
Relationship between Information Integrity and Technology Utility
|
| Information Integrity is ensured when the transaction information is properly described and has not un dergone any unscrupulous changes without the knowledge or consent of the end-users. Information Integrity may positively influence the Technology Utility in two ways. Firstly, when the end-user observes the transaction information and is ensured that output is in the expected format, the end-user seems to be relieved which may lead to less mental trauma or cost. Secondly, the end-user may gather some relevant information from the transaction information, which may be useful for their other purposes leading to additional benefits. So in either of the cases, with less cost and more benefits the Technology Utility may be increased. |
| As per the results, Customization and Security didn’t influence Technology Utility. Customization and Security seem to be mechanisms provided in the interface whereas Organization of information, Transaction Facility and Information Integrity seem to reflect the outcomes of the interface. From the results, it appears that the end-users seem to be more interested in the outcomes rather than the mechanisms. This may be due the Internet banking experience of the respondents, most of whom are having more than 2 years of experience. Hence they may be interested in the outcomes of the interface rather than the mechanisms. However this result should not undermine the importance of these features. The designers may consider customization and security as the ingredients for the features like Organization of Information, Transaction Facility and Information Integrity which seem to be more apparent to the end-users. They may use customization and security to enhance seemingly apparent features. For instance, customized links in the interface may enhance Organization of Information and Transaction Facility whereas the security mechanism may improve Information Integrity. |
| The relationship between Information Integrity and Technology Utility is stronger for end-users with low self-efficacy than those with high self-efficacy. People with low self-efficacy may be inherently scared of using the Internet banking interface due to lack of confidence. They may look for assurance from the interface that information and status of their transactions are not changed without any logical reason. If the transaction information is displayed clearly without any ambiguity, it may boost their confidence in the interface. This in turn, may motivate them to use the interface. On the other hand people with high self-efficacy seem to compensate the lapses in the Information Integrity with their confidence. They don’t seem to be severely affected even if the transaction information displayed is not according to their expectations. People with high self-efficacy seem to be in a much better situation to handle the panic alarm than those with low self-efficacy. |
| The relationship between Organization of Information and Technology Utility is stronger for women than for men. The need for a well-organized Internet banking interface to derive utility from the interface seems to be more prevalent in women than in men. This finding could be attributed to the differences in information processing capabilities of men and women. According to past research studies by Meyers-Levy(1988) ,Babakus and Yavas (2008) which examined the role of gender in making judgments and taking decisions , men are more task or goal-oriented and women are more relationship-oriented. The results are consistent with the results obtained by Noble et al.(2006) according to which women tend to exhibit stronger desire for affiliation and place high value on interaction with store employees which provides them with informational and interpersonal cues than men. |
| The relationship between Transaction Facility and Technology Utility is stronger in case of younger age group (age <=30) than the older age group (age >30). The reasons for this result can be many. One possible reason is that the younger age groups may be more enthusiastic in exploring new transaction avenues available at their finger tip. The other compelling factor could be their busy schedule at their work place which forces them to use the different transaction facilities provided at the interface as to save time, cost and effort. The older age group in turn may prefer interacting with the bank employee to get the matter sorted rather than using self-help features provided in the interface. Further the results of this study show that the relationship between Transaction Facility and Technology Utility is insignificant for the older age group. |
Managerial Implications
|
| The key variables which drove Technology Utility of the Technology interface were Organization of Information, Transaction Facility and Information Integrity. Managers and designers of the Technology interface need to concentrate on strategic practices which may improve the perception of the end-users about these key variables. Based on the results, the following practices are suggested. |
| Move Recording facility- This should be provided in the interface which will help the end-users recall the transaction and browsing activities carried out during the last login. This is basically recording all the moves the end-user had carried out during the last login. This type of facility is provided in new communication service called “Google Wave”. The advantage of this facility is that the end-user is assured that no unscrupulous activities are carried out without the knowledge of the user. |
| Book Marking Favorite link facility- The end-user may be provided with web links to various services and other e-commerce sites with which the bank has the tie-up for the payment process. To facilitate easy and quick search to the regularly used services or sites, a book marking facility should be provided in the site itself which will store the favorite links. These links can be displayed whenever the end-user logs in. The book marking facility can be further improvised to make it a social computing tool wherein the end-user can get to know how many users have the same link as their favorite and what are the other favorite links of those end-users subject to the condition that they have permitted to share their favorite links. This type of facility is provided by social bookmarking sites like “Delicious”. |
| On demand display of transaction information- In order to save space, the transaction information is quite obscurely displayed. This may raise the anxiety level of the end users with low Self- Efficacy. So, even if it is not feasible to display the complete details, at least the complete details may be shown as a comment or as a pop-up screen when the end-user places the cursor or the mouse arrow over the transaction information |
Limitations and future research directions
|
| Results indicated the relationship between Customization and Technology Utility; the relationship between Security and Technology to be insignificant .The relationship between Organization of Information and Technology Utility; relationship between Transaction Facility and Technology Utility; relationship between Information Integrity and Technology Utility were significant. Thus Customization and Security seem to be less apparent to the users compared to Organization of Information, Transaction Facility and Information Integrity while deriving utility from the interface. This may suggest that Customization and Security are likely to influence Technology Utility through Organization of Information, Transaction Facility and Information Integrity. Future studies can investigate the mediating role of Organization of Information, Transaction Facility and Information Integrity in the relationships; between Customization and Technology Utility; and between Security and Technology Utility. |
| Most of the responses in this study were obtained online. However it would be interesting to compare the results obtained based on the online responses with the results obtained based on the offline responses. |
| Finally, the research model used in this study can be tested for various technology interfaces such as the mobile banking interface and e-commerce sites. In case of e-commerce sites, the visual appeal of the interfaces, the playfulness of the websites in terms of music, games can also be considered as factors influencing the utility of the interface. This type of utility is often hedonistic in nature i.e. the utility gained in terms of pleasure rather than improvement of productivity or reduction in costs. The research model in this study considered the utilitarian perspective rather than the hedonistic view of technology utility as well characteristics of the technology interface. While considering the hedonistic view, some more variables related to visual appeal, pleasure, playfulness can be included in the research model and tested. |
CONCLUSION
|
| The significance of this study lies in its potential contribution to both literature and managerial practices. From the research perspective, this research will help to identify the various technological interface dimensions and their relation with the utility and usage of the technological interface, paving the ground for further empirical research in this field. From the business standpoint, such knowledge will help in the design and management of the technological interface according to the needs of the customer and the design of appropriate training and support programs. |
Tables at a glance
|
 |
 |
 |
 |
 |
| Table 1 |
Table 2 |
Table 3 |
Table 4 |
Table 5 |
|
 |
 |
 |
 |
| Table 6 |
Table 7 |
Table 8 |
Table 9 |
|
 |
 |
 |
 |
| Table 10 |
Table 11 |
Table 12 |
Table 13 |
|
Figures at a glance
|
 |
| Figure 1 |
|
References
|
- Agarwal, R. & Prasad J. (1999). Are Individual Differences Germane to the Acceptance of New Information Technologies? Decision Sciences, 30 (2), 361-391.
- Babakus, E. &Yavas, U. (2008).Does customer sex influence the relationship between perceived quality and share of wallet? Journal of Business Research,61 (9), 974-981
- Dabholkar, P.A. &Bagozzi, R.P. (2002). An Attitudinal Model of Technology-Based Self-Service: Moderating Effects of Consumer Traits and Situational Factors. Journal of the Academy of Marketing Science, 30 (3), 184-201.
- Davis F.D.(1989). Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology. MIS Quarterly, 13 (3), 319-340.
- Davis, F.D., Bagozzi, R.P. &Warshaw, P.R. (1989). User acceptance of computer technology: A comparison of two theoretical models. Management Science, 35 (8), 982-1003.
- Davis, F.D.(1993). User acceptance of information technology: system characteristics, user perceptions and behavioral impacts. International Journal of Man Machine Studies, 38, 475-487.
- Fishbein,M. &Ajzen,I.(1975). Belief, Attitude, Intention and Behavior: An Introduction to Theory and Research. Addison-Wesley.
- Flowerday, S. &Solmes, R.V.(2005). Real time Information Integrity = System Integrity + Data Integrity + Continuous Assurances. Computers and Security, 24 (8), 604-613.
- Hair, J.F., Black, W.C., Babin, B.J., Anderson, R.E. &Tatham, R.L.(2006). Multivariate Data Analysis (6th ed.). Pearson Education.
- Igbaria, M., Guimaraes, T. & Davis, G.B. (1995). Testing the determinants of microcomputer usage via a structural equation model. Journal of Management Information Systems – Special section: Navigation in information-intensive environments, 11(4), 87-114
- Lee, Y.W., Strong, D.M., Kahn, B.K. & Wang, R.Y. (2002). AIMQ: a methodology for information quality assessment. Information and Management, 40 (2), 133-146.
- Loiacono, E.T., Watson, R.T. & Goodhue, D.L.(2007). WebQual: An Instrument for Consumer Evaluation of Web Sites. International Journal of Electronic Commerce, 11 (3), 51-87.
- Meuter, M.L., Ostrom, A.L., Roundtree, R.I. &Bitner, M.J. (2000). Self-Service Technologies: Understanding Customer Satisfaction with Technology-Based Service Encounters. Journal of Marketing, 64, 50-64.
- Meyers-Levy, J.(1988).The Influence of Sex Roles on Judgement . Journal of Consumer Research, 14 ( 4), 522-530.
- Moore,G.C. &Benbasat,I (1991). Development of an Instrument to Measure the Perceptions of Adopting an Information Technology Innovation. Information Systems Research, 2 (3), 192-222.
- Noble, S.M., Griffith, D.A. &Adjei, M.T.(2006). Drivers of Local Merchant Loyalty: Understanding the Influence of Gender and Shopping Motives. Journal of Retailing, 82 (3), 177-188.
- Nunnally, J. C. 1978. Psychometric Theory. McGraw-Hill, New York
- Orlikowski, W. J. &Iacono, C.S. (2001). Research commentary: Desperately seeking the “IT” in IT researches—A call to theorizing the IT artifact. Information Systems Research, 12 (2), 121–134.
- Palmer, J.W.(2002), Website Usability , Design and Performance Metrics, Information Systems Research,13 (2), 151-167
- Ratneshwar, S. & Shocker, S.D.(1999). Product, person and purpose: Putting the consumer back into theories of dynamic market behavior. Journal of Strategic Marketing, 7, 191-208.
- Tsiakis, T., Sthephanides, G. (2005).The concepts of security and trust in electronic payments. Computer and Security, 24,10–15.
- Venkatesh, V.(2000). Determinants of Perceived Ease of Use: Integrating Control, Intrinsic Motivation, and Emotion into the Technology Acceptance Model. Information Systems Research,11 (4),342-365.
- Venkatesh,V. & Davis, F.D.(2000). A Theoretical Extension of the Technology Acceptance Model : Four Longitudinal Field Studies. Management Science, 46 (2), 186-204.
- Venkatesh, V., Davis, F.D. & Morris, M.G.(2007). Dead or Alive? The Development, Trajectory and Future of Technology Adoption Research. Journal of the Association for Information Systems, 8 (4), 267-286.
- Venkatesh, V. &Bala, H.(2008). Technology Acceptance Model 3 and a Research Agenda on Interventions. Decision Sciences, 39 (2), 273-315.
- Wixom B.H. & Todd P.A.(2005). A Theoretical Integration of User Satisfaction and Technology Acceptance. Information Systems Research, 16 (1), 85-102.
|