ISSN: 1204-5357
ISSN: 1204-5357
Olasanmi, Omoneye Olufunke, Lecturer
Department of Management and Accounting, Faculty of Administration, Obafemi Awolowo University, Ile-Ife, Nigeria
E-mail: neyeolasanmi@yahoo.com
Olasanmi Omoneye O. is a lecturer in the Department of Management and Accounting, Faculty of Administration, Obafemi Awolowo University, Ile-Ife, Nigeria. Her areas of interest include E-commerce, Management Information Systems, Electronic Marketing, and Information Systems Security. She is currently carrying out analysis on issues relating to IT innovations and customer satisfaction. Her publications include areas such as e-governance, ICT sustainability, and e-education.
Visit for more related articles at Journal of Internet Banking and Commerce
The increase in the use of the information and communication technology (ICT) facilities such as computers and the Internet in the perpetration of criminal activities like spamming, credit card frauds, ATM frauds, phishing, identity theft, denial-of-service, and a host of others has lend credence to the view that ICT is contributing to crime in the banking sector. A greater understanding of such computer crimes may complement existing security practices by possibly highlighting new areas of counter measures. This paper thus assesses whether these crimes can be totally eradicated or not and whether the new generation banks experience more computer crimes than the old generation banks in Nigeria. Based on the findings of this study, the paper concludes that total eradication of computer crimes is not possible but can be highly reduced if internal control measures are adequately put in place within a bank’s organizational structure and that new generation banks seem to experience more crimes than their old generation counterparts due to the fact that majority of their services, which are automated, are subjected to technological changes at a rapid rate.
Computer crimes, Control measures, the Internet, ICT
When banks and other organizations began to be computerized in Nigeria over a decade ago, little did they know that they were setting the pace in computer crimes age. Today, the computer is used everywhere, with individuals and corporate bodies having now found its use compelling. With its usage, the computer and the Internet have changed working attitudes in the banking industry. If there is anything that has necessitated the use of computers in banks, it is the large number of transactions they process. Since banks handle large numbers of transactions on a daily basis, the use of computers and the Internet have become inevitable.
Essentially, computers and the Internet in banks facilitate records of customers’ transactions and transfer of monetary values. With the computer and Internet facilities put in place, customers communicate directly with their banks to pay bills, transfer funds, inquire about account balances, and perform all sorts of services offered by such banks. This development is extremely profitable to all but organizations employing computers and the Internet to improve business processes should not ignore the fact that it also improves efficiency both for the company and the criminally-minded.
It should be noted that before the development of computer crimes, there had been occurrences of bank-related crimes. These traditional crimes include the typical ones such as bank robbery, false statements to a bank in order to obtain a loan, misapplication or embezzlement of bank funds, false entries in a bank’s books, bank bribery and bank fraud. There is a marked difference between these traditional crimes and the modern-day computer crimes, as some of the traditional crimes require violence or a threat of violence. In addition, the perpetrators of traditional crimes were more visible and detection of such crimes was relatively easy. Inasmuch as the characteristics of these crimes are different, the motivations of the criminals are much the same; people still rob banks because they need the money stored there. The advent of the computer has only provided another means and opportunity to such criminals.
The computer was invented to hasten data processing with effortless ease. However, as the understanding of the use of the computer has increased across various levels of knowledge, so as its use for committing crimes increased. Today, not only young whiz kids hack into computers, Information Technology (IT) professionals have joined the league. A new breed of white collar criminals has emerged. More mature offenders, often with a background in the IT industry, are infiltrating systems one way or the other. The introduction of the Internet has heightened the threat of these crimes. Everyone is susceptible to computer crimes once you have a computer and a direct or indirect access to the Internet.
The increasing rate at which systems can connect together to share information has not only increased the number of prospective victims of computer-related crime, it also increased the number of prospective offenders. Yet the complexity of these crimes and the elusive nature of computer criminals have made it increasingly difficult to detect or prevent these crimes. Computer crimes have quickly increased in recent years and have overtaken the ability of the government and the various sectors to fully protect their systems.
Estimating the incidence, prevalence, cost, or some other measure of computer related crime is a difficult challenge because such crimes are not easily detected and even when detected, reports to the appropriate authorities are not always made. Businesses do not always want to report problems because there is a perception that their information will be disclosed publicly, which could, in turn, cause harm to their business. Effective responses are therefore required to tackle the issue of computer crimes, particularly given its global dimensions on the Internet.
This research work seeks to bring to light the dangers or threats, possible counter measures and control of computer crimes in the banking sector. The objectives of this study are to:
i. determine the types of computer crimes experienced by some selected banks
ii. identify the factors contributing to the occurrence of such crimes
iii. identify the most prevalent of the computer crimes
iv. proffer control measures to curb computer crimes
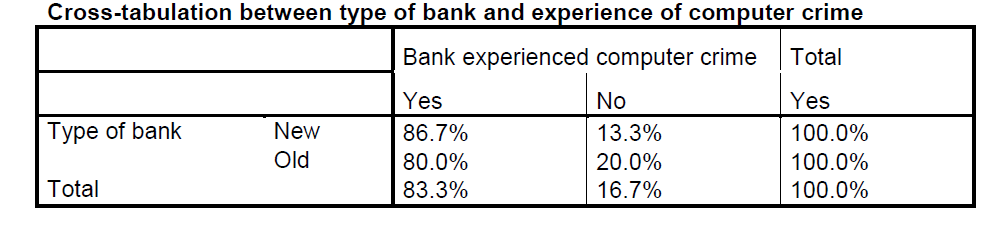
Ho: Old generation banks do not experience more computer crimes as new generation banks
Ho: Computer crimes cannot be totally eradicated in banks
A computer crime is an illegal activity that is executed via a computer. It is an act committed in violation of criminal or civil codes using electronic or digital technologies for unauthorized activities and transactions. It involves access to the whole or any part of an Information Technology system without right. In the banking sector, it could mean manipulating banking systems to make unauthorized identity theft with reference to ATMs.
Computer crime is a crime in which the use of or access to a computer or its components (terminals, networks and so on) is an essential element; that is, the crime could not have been committed without the use of a computer. Computer crime mainly consists of unauthorized access to computer systems, data alteration, data destruction, or theft of intellectual property. Almost all computer crimes involve unauthorized access or access exceeding the authorisation. The hacker, by stealing or bypassing the password and other security features, breaks into the computer system. The intention may be to commit financial fraud or to steal some sensitive data.
Computer crimes are usually targeted at networks (generally defined as a specific type of relation linking a defined set of persons, objects, or events). Technology creates dependencies that evolve to interdependency; a significant attack on one can directly impact others (cascade effect). Computer crimes have quickly increased in recent years and have overtaken the ability of the government and the private sector to fully protect their systems. The introduction of the internet has heightened the threat of these crimes. Not only does the increasing connectivity increase the number of prospective victims of computer-related crime, it also provides prospective offenders with greater access and wider opportunities.
A computer crime is very similar to a normal crime. The only difference is the means in which the act is carried out. An individual can commit theft, trespassing, embezzlement and fraud all on a computer system.
a) Invisibility/Anonymity of offender:
Tracing perpetrators of these crimes require a degree of computer know-how that is usually lacking in most organizations. These criminals are not like the traditional criminals that physically rob a bank; pin-pointing who exactly is committing such crimes is extremely difficult.
b) Lack of victim awareness:
In most cases, victims of theses crimes are not even aware that they have been infiltrated. An individual with a personal computer might not even know when his/her system has been infected with a virus or when his/her account has been tapped into. It is much worse for large organizations because they don’t usually have adequate monitoring systems that can detect such crimes.
c) Unwillingness to report:
Most organizations tend to put a lid on the crimes being perpetrated in their organization for various reasons such as to avoid negative publicity, incidents not serious enough, or their company was not specifically targeted etc.
d) Intangibility of digital goods, evidence, value:
Computer crimes can be seen as virtual crimes; they can’t be touched. The criminal is not seen physically committing the crime, the goods being stolen are not physical good and prosecution for these crimes is difficult as there is no tangible evidence to present.
Banks have to decide what security measures they are prepared to invest in and what trade-offs they are prepared to make when it comes to computer crimes. Computer crimes are fast and growing because the evolution of technology is fast, but the evolution of law is slow. Controls can be instituted within industries to prevent such crimes. Protection measures such as hardware identification, access controls software and disconnecting critical bank applications should be devised. However, it should be noted that computers don't commit crimes; people do. The perpetrator's best advantage is ignorance on the part of those protecting the system. Proper internal controls reduce the opportunity for fraud.
While a variety of countries are passing legislation relating to computer crime, the awareness of the situation is still lost on our own government. To be able to effectively tackle this problem, organizations need to make the public aware of their crime experiences.
Most computer-related crimes are prevalent in cities with predominantly literate individuals since some level of literacy and intelligence are required to commit such crimes. Thus, the study area will thus focus on a town with big institutions and major banks. Eight banks are purposively selected for this survey, four banks representing new generation banks while the other four represents old generation banks. Data for the study is collected through the administration of questionnaires and unstructured interviews with some workers of the selected bank.
Data collected was analyzed using SPSS software, version 15. The analysis method included frequency tables, pie charts, bar charts, and cross-tabulations while Chi-square was employed as the inferential analytical tool for the testing the hypotheses of the study.
Data was gathered from 40 respondents using the purposive sampling method. Purposive sampling method is a form of non-probability sampling in which the population elements are intentionally selected purely at the discretion of the researcher. The power of purposive sampling lies in selecting information rich-respondents for in-depth analysis related to the central issues being studied (Trochim, 2006). These respondents have one time or the other experienced computer crimes, perpetrated within or outside the bank premises by either customers or bank workers.
Of the 40 respondents selected for the study, 30 respondents (75 percent) actually participated in the research. The remaining 25 percent (10 respondents) were either unwilling to take part in the research or were too busy to fill the questionnaire; the unwilling ones opined that their responses might view their banks in a bad light and opted out of the research.
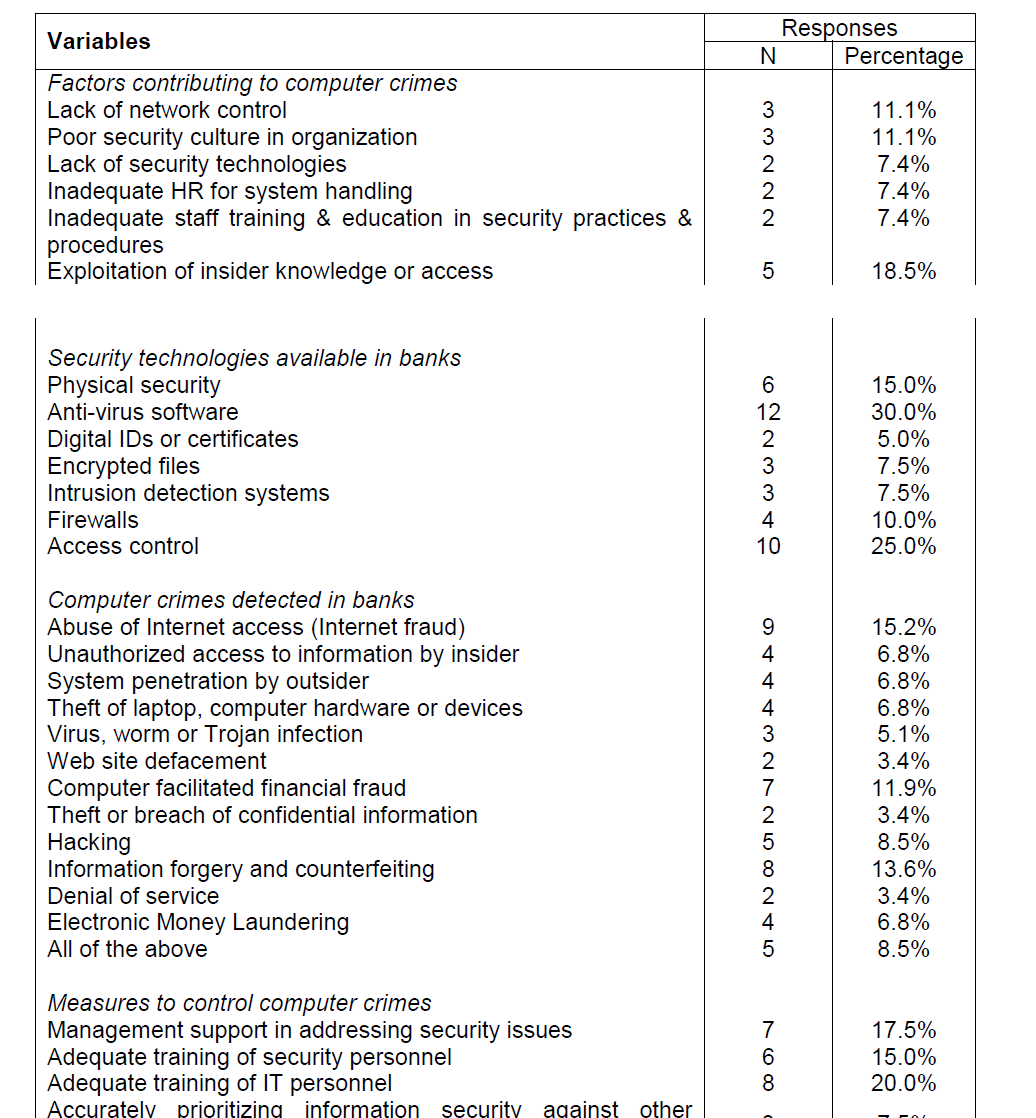
83 percent of the respondents acclaimed that they have experienced some forms of computer crimes. 22 percent of the respondents indicated that the crimes experienced were perpetrated by people outside their organization while 33 percent indicated that the crimes were perpetrated by internal members. 36 percent believed that the internal crimes were carried out to illicit financial gains and to settle some personal grievances within the banking arena. 53 percent of these crimes were often carried out through the Automated Teller Machine (ATM), 34 percent through Internet access, while 13 percent were executed on computer systems files.
The highest form of these crimes is internet fraud (15 percent), followed by information forgery and counterfeiting (13 percent) and computer facilitated financial fraud (12 percent). Other crimes include hacking by outsider (9 percent), virus/Trojan infection (5 percent) and denial of service (3 percent). These crimes caused the organizations huge financial losses and even loss of customers.
Hypothesis Testing
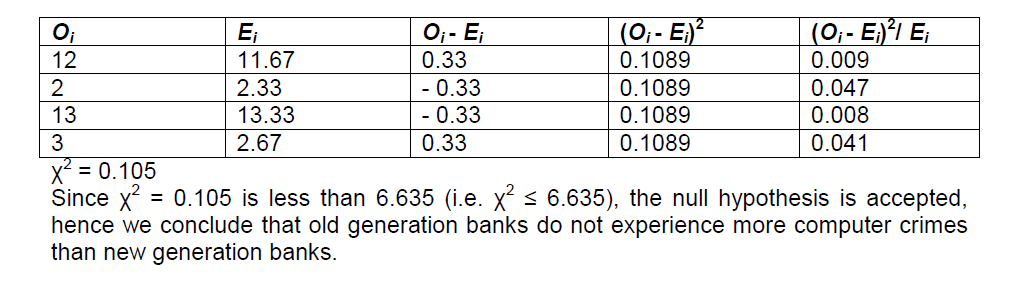
Hypothesis 1 ( Ho): Old generation banks do not experience more computer crimes as new generation banks
Level of significance = 0.05
Decision Rule: Reject the null hypothesis if χ2 ≥ 6.635 where
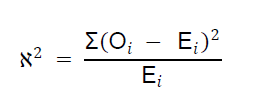
and 6.635 is the value of χ2.05, 1
Hypothesis 2 ( Ho): Computer crimes cannot be totally eradicated in banks
Level of significance = 0.05
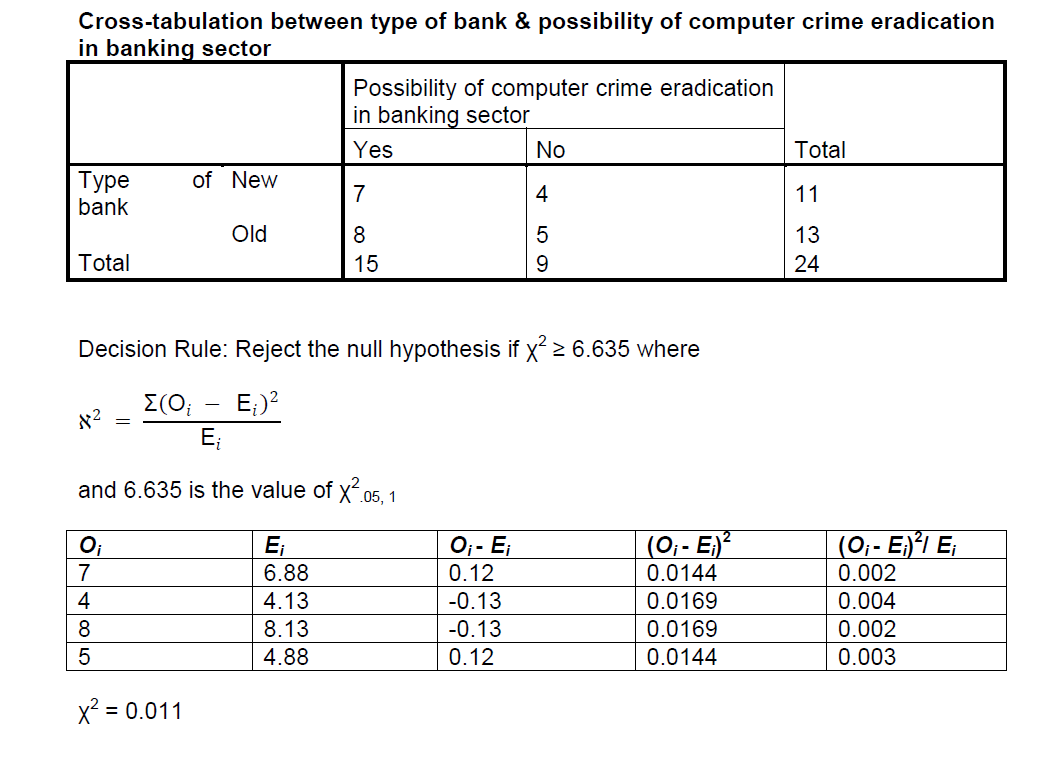
Since χ2 = 0.011 is less than 6.635 (i.e. χ2 ≤ 6.635), the null hypothesis is accepted, hence we conclude that computer crimes cannot be totally eradicated in Nigerian banks.
From the data gathered from the respondents in Ile-Ife metropolis, it is evident that most banks have at one time or the other experienced computer crimes in one form or the other. The exact rate of crimes experienced by each bank and the banking sector as a whole cannot be accurately measured at this point, as most banks do not report the computer crimes detected for publicity reasons. These crimes are not being perpetrated by outsiders only, in fact, majority of the perpetrators are reported to have an insider working with them. The perpetrators of these crimes are successful most of the time not just because of their know-how but some organizations make it easy by neglecting staff training and knowledge about computer security or not investing in the right technological equipments. Also, some bank customers aid the occurrence of these crimes by being lackadaisical about their bank accounts, ATM cards and personal information, thereby making themselves easy targets for offenders. Bank customers have to be more careful about the bank’s properties in their care.
A major challenge of the banking organization is keeping up to date with changes in technology in spite of the fact that they keep increasing their expenditure on computer security; it seems not to be adequate to cope with the rate of changes in technology. Computer security measures can however be beefed up by using anti-virus software, access control, firewalls and by employing qualified IT or IT-security staff. Added to these measures should be the adequate training of staff on computer security. As a result of all the factors militating against computer security of organizations, the tested hypothesis showed that the total eradication of computer crimes is not possible. It can however be reduced through public education, compliance using effective security technologies, having law enforcement agents equal in technical skill to computer criminals, and the establishment of a balanced standard for the prosecution of computer criminals.
Based on the findings of this study, it can be concluded that computer crimes are being experienced by the Nigerian banking sector. These crimes are not harmless; they are causing banks financial loss which would ultimately have an adverse effect on the economy. Most banks have measures in place to manage the occurrence of computer crimes but based on the fact that technology advance on a daily basis, bank management should try to keep up with these advances in other to efficiently combat computer crimes and reduce them to the barest minimum.
Copyright © 2026 Research and Reviews, All Rights Reserved